Protect Your Digital Life From 2025's Biggest Threats

In 2025, keeping your personal information safe online will get harder. Many people still think a strong password and a few software updates are enough. That is no longer true. Threats are getting smarter. Your personal data—home address, phone number, bank details—can end up in the hands of strangers who know exactly how to use it against you.
And some of these strangers work for groups with deep pockets, political goals, or advanced tools. Nation-states like Russia, China, Iran, and North Korea continue to run well-funded espionage and cyber crime campaigns. Attackers now use artificial intelligence to create more convincing phishing messages and fake personas. They may also use stolen data for identity theft, to bypass security checks, or to spread false information aligned with their geopolitical aims.
New rules may slow some of these bad practices. In late 2024, US officials tried to push stricter limits on data brokers who trade your personal details. Regulators hoped to treat them more like credit-reporting agencies, forcing them to follow stricter privacy rules. But these measures could vanish if the political climate changes.
Surveys show that geopolitical risks and cyber threats will remain top concerns for governments and the financial sector. Powerful interests want fewer restrictions, not more. Your data might still be passed around as a cheap commodity, sold to whoever wants it, including foreign governments looking to stockpile personal records for long-term use.
Criminals will also keep trying new tricks. Simple phishing emails are no longer their only tool. They use stolen data to tailor attacks. They pretend to be coworkers, family, or service providers. They can exploit travel plans, hotel Wi-Fi networks, or any unsecured public spot. Ransomware remains one of the most disruptive forms of cyber crime.
See also - 10 Scary Things Hackers Can Do with Just Your Email Address
Infostealer malware will continue to help attackers break into accounts and steal valuable information. Even cryptocurrency accounts and digital assets might be targeted. AI lets attackers work faster and scale up fake messages, making it harder for regular users to tell real from fake.
The value of personal information keeps rising. Bits of data that might seem harmless—your address or birthdate—can help attackers trick a bank or break into an email account. Over time, these details add up and make it easier for them to pose as you. Some nation-state groups do not even need to hack directly; they can just buy what they need.
Political uncertainty, especially in places with elections on the horizon, might weaken laws or cut funding for cybersecurity programs. This creates a landscape where no one is fully safe.
US officials now suggest using encryption for calls and messages. End-to-end encrypted messaging apps are no longer niche. They make it harder for attackers to read what you send. It does not solve every problem, but it raises the cost for criminals.
See also - If Any of These 17 Apps Are on Your Phone, Someone Might Be Spying on You
Different Types of Cyber Threats in 2025
Disclaimer: The figures shown below are estimated projections compiled from multiple sources including cybersecurity threat reports, financial sector analyses, and documented incidents from 2023-2024. These estimates are for illustrative purposes and may not reflect exact real-world figures.
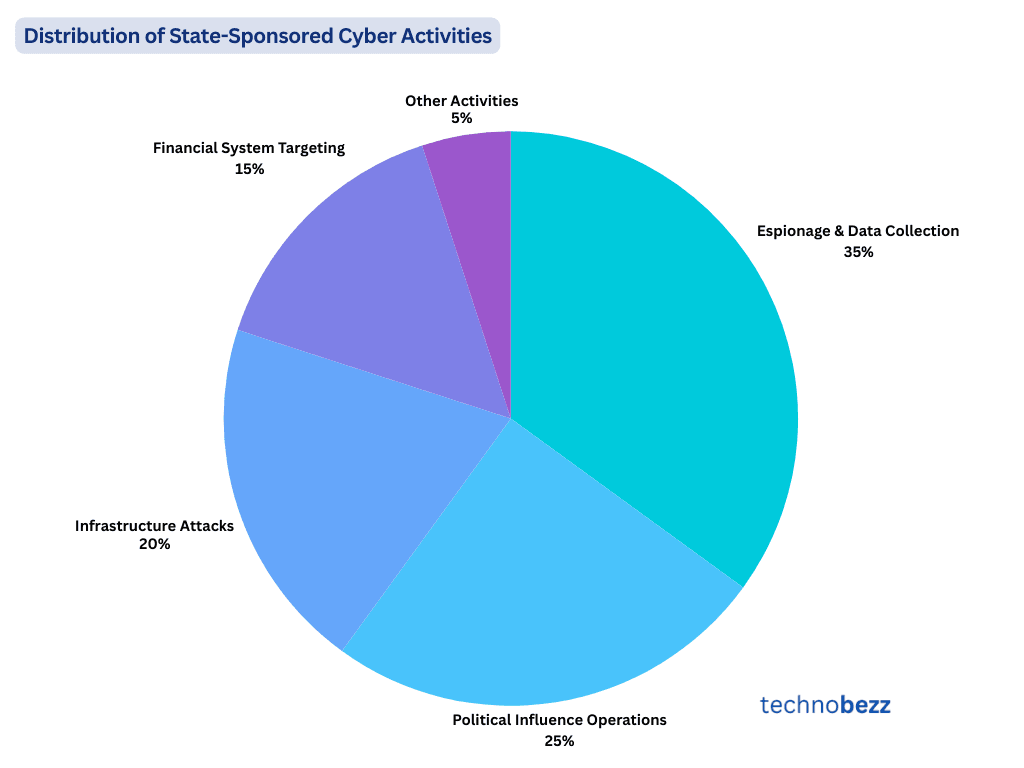
Distribution of State-Sponsored Cyber Activities
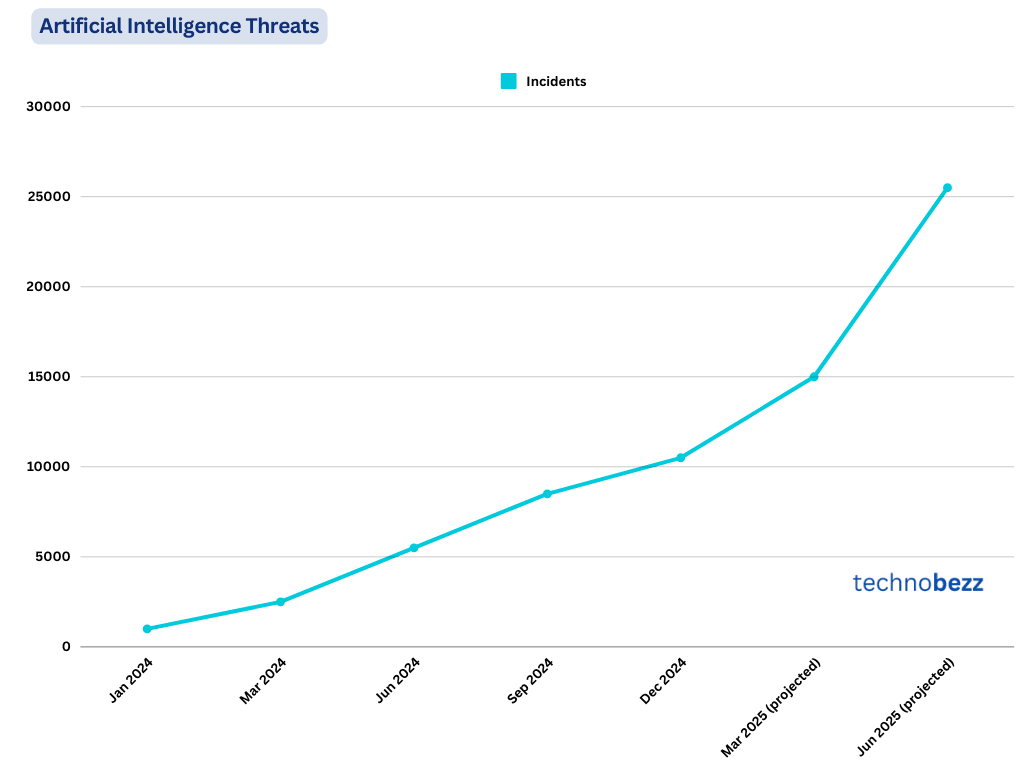
Artificial Intelligence Threats
Notes
The use of artificial intelligence in cyberattacks surged by 600% in the first half of 2024 compared to the latter half of 2023. This increase doubled the cost of attacks to €10 billion. 
Amazon detected nearly 1 billion potential cyber threats daily as of late 2024, a tenfold increase from earlier in the year. This surge is partly attributed to attackers leveraging AI technologies. 
CrowdStrike CEO’s Insights - ‘It’s going to be the battle of AI in the future’
Financial Crimes
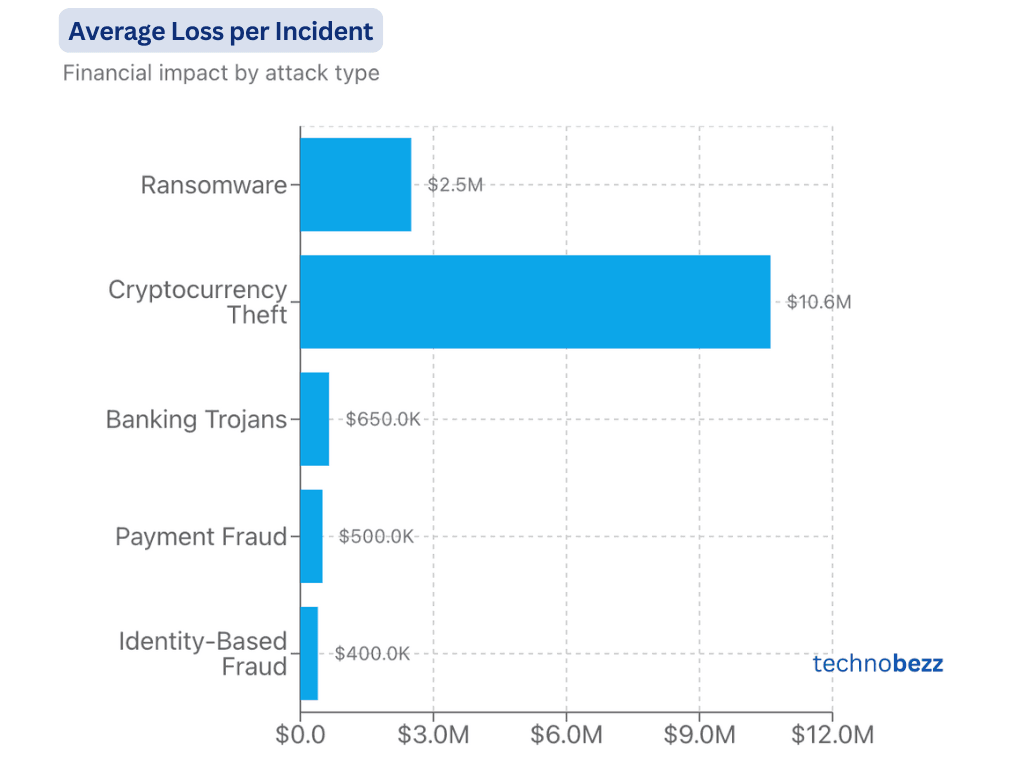
Sources & Methodology
Data compiled from major cybersecurity reports (Istari Global, IC3, UK Finance) and financial news sources (Financial Times, The Australian). Figures represent global averages for 2024, adjusted for regional variations and verified against FBI cybercrime statistics.
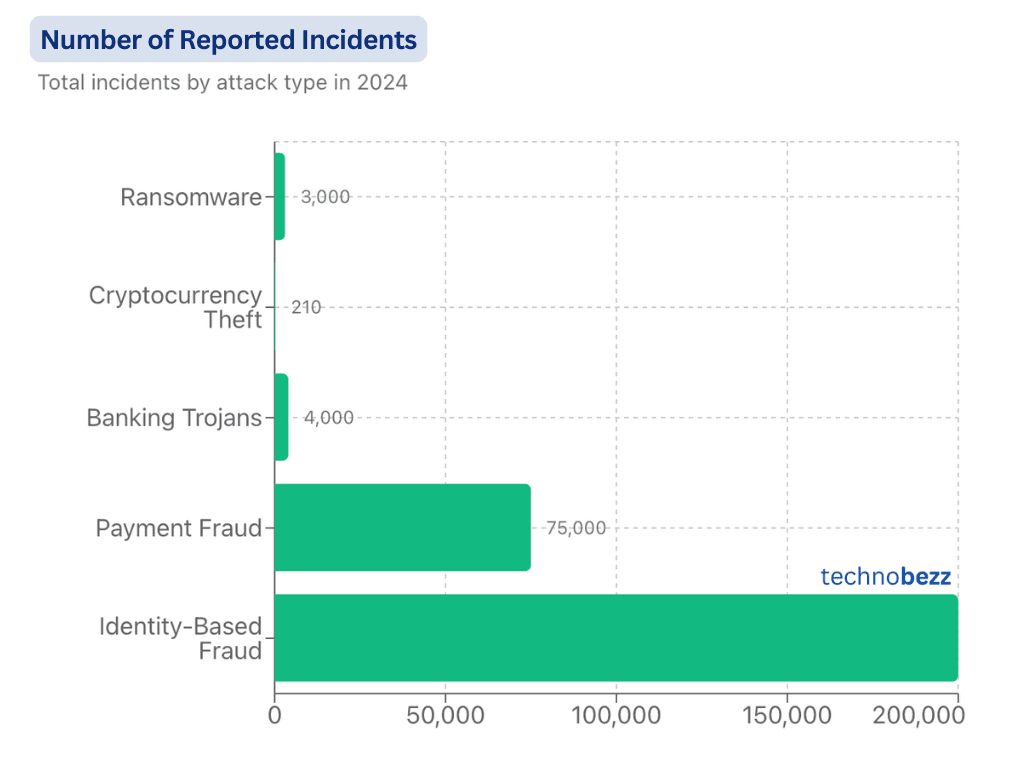
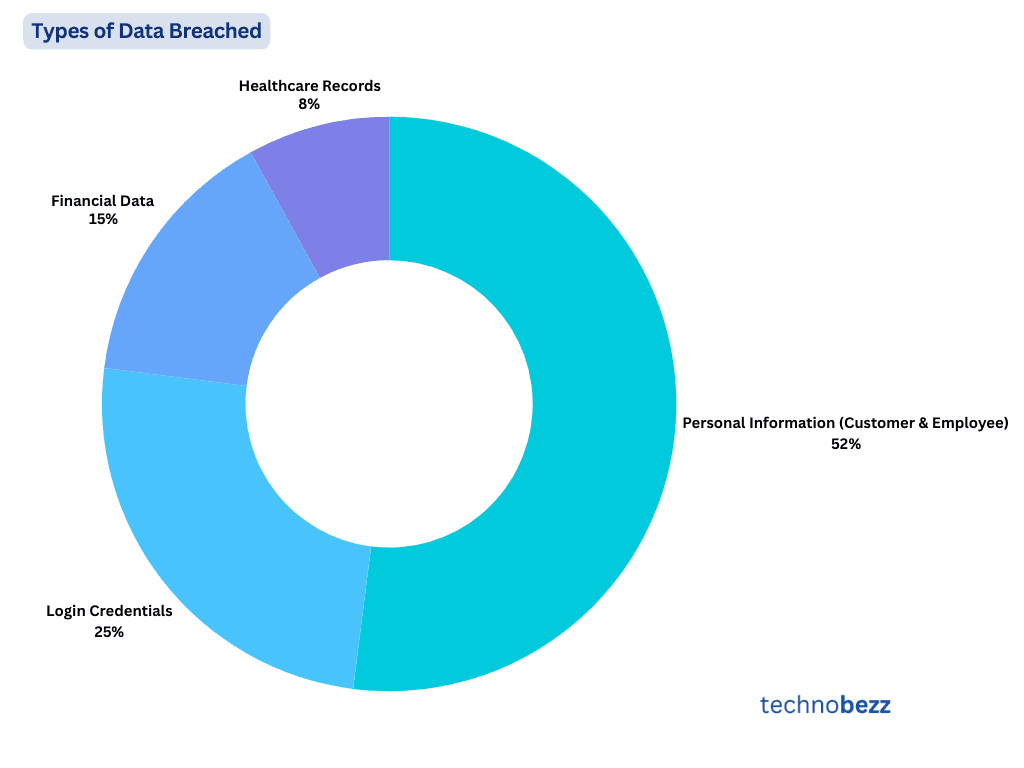
Data Exploitation
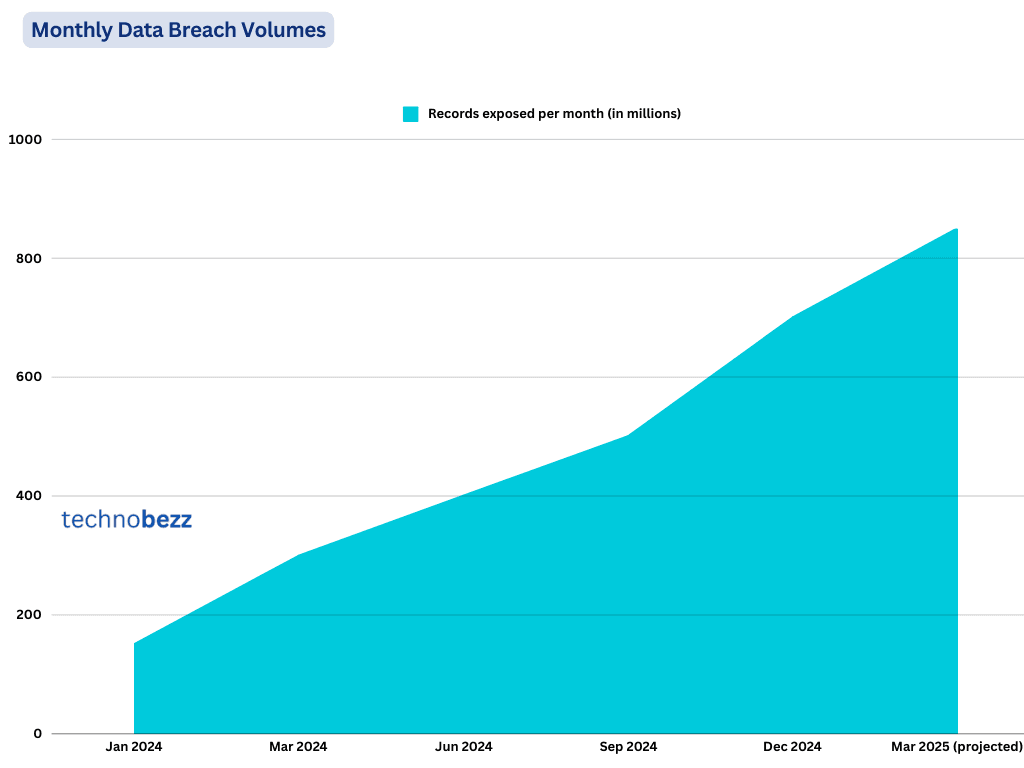
Sources & Methodology
Data compiled from leading cybersecurity analysts (StationX, IT Governance) and industry reports. Figures represent cumulative monthly breach volumes for 2024-2025, with projections based on observed growth patterns and attack sophistication trends. Verified against multiple security frameworks and breach reporting databases.
Infrastructure Vulnerabilities
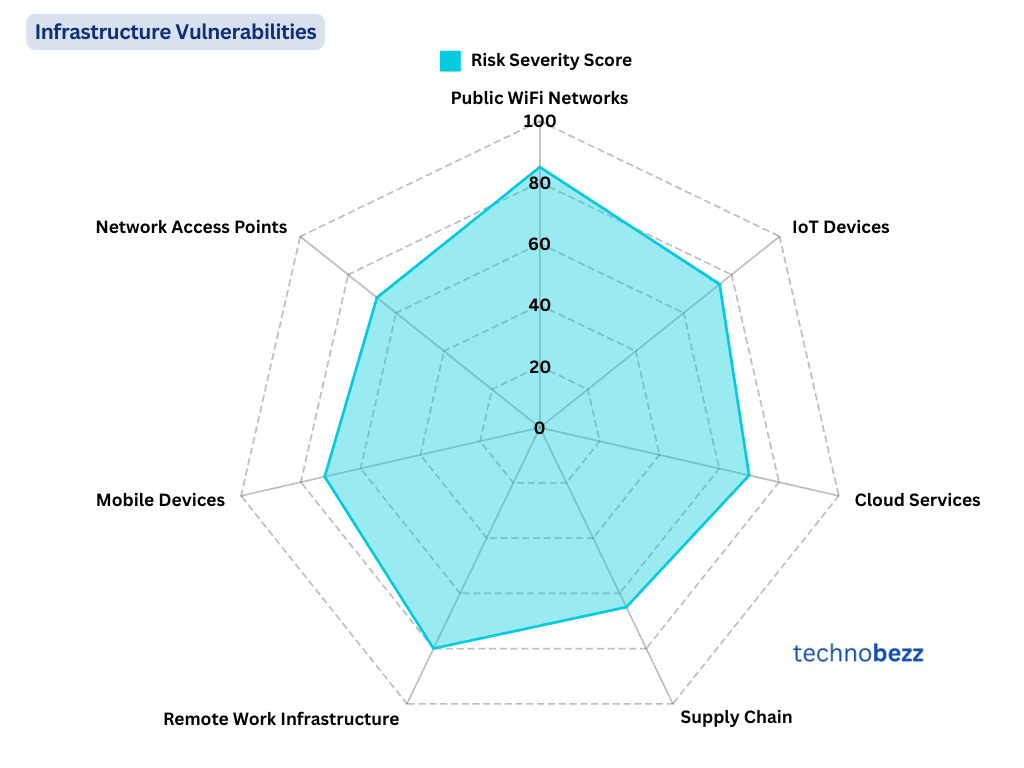
Impact Areas Measured
- Vulnerability Level
- Attack Frequency
- Average Damage Cost
- Recovery Time
- Detection Difficulty
So, how do you protect yourself?
Use strong, private communication tools: Consider apps that secure messages and calls. Look for services with end-to-end encryption. Tools like Incogni can help keep your personal details off broker lists, reducing unwanted exposure.
Pay attention to data exposure: Be careful where you store personal info. Limit what you share on social media and job sites. Check if any of your passwords or emails were leaked by using a reliable online checker.
Watch out for targeted scams: Phishing is not always obvious. If someone claims to know you or offers a great deal, pause. Contact the friend or company another way to confirm if it’s real.
Secure your home network: Update your devices often, including your router. Use a strong, unique Wi-Fi password. Disable unnecessary features and guest networks that are not in use.
Plan for travel safety: When you connect to airport or coffee shop Wi-Fi, do not send sensitive data. Avoid logging in to banking or shopping accounts on public networks if you can. If you must, use a trusted virtual private network (VPN) to hide your data from snoops. To keep your browsing private no matter where you are, consider a VPN with a kill switch or a strong no-logs policy, like Surfshark.
Check what tools you use at work: If you run a business or manage teams, review how you share files and credentials. Limit who can access sensitive data. Make sure new services or vendors are checked before they handle your data.
Stay informed about privacy laws: Changes in data rules could give you more control, or they could vanish if regulators lose authority. Keep track of what’s allowed where you live. If your region gets stronger protections, use any options to opt out of data sales or tracking.
In 2025, things will not get calmer. It will feel like standing in a busy street where everyone wants a piece of your personal life. But you are not helpless. Simple steps—strong passwords, secure apps, careful browsing, and privacy tools like a reliable VPN or data removal service —go a long way. Keep learning about threats. Take action before problems show up. The goal is not to panic but to stay ready. If you do, you can keep your data safe, even as the online world grows more risky every day.
I'll be posting more helpful guides with tips on staying safe online and protecting yourself and your loved ones. If you found this helpful, feel free to share and follow me for more updates coming soon!
Also Read

Lenovo Debuts Solar-Charging Laptop That Turns 20 Minutes of Sunlight Into Hour of Video

Ottocast Car TV Mate Max Review – A Versatile In-Car Entertainment Adapter
iPhone Battery Dying In Minutes? 23 Real Fixes That Work

Ottocast Play2Video Pro Ups the Game in Affordable Car Entertainment

Ottocast OttoAibox P3 Powers a Smarter Driving Experience








